用户:幻想乡的反逆者/沙盒
| 互联网协议套组 |
|---|
| 应用层 |
| 传输层 |
| 网络层 |
| 链接层 |
Secure Shell(安全外壳协议,简称SSH)是一种加密的网络传输协议,可在不安全的网络中为网络服务提供安全的传输环境[1]。SSH通过在网络中建立安全隧道来实现SSH客户端与伺服器之间的连接[2]。虽然任何网络服务都可以通过SSH实现安全传输,SSH最常见的用途是远程登录系统,人们通常利用SSH来传输命令行界面和远程执行命令。使用频率最高的场合类Unix系统,但是Windows操作系统也能有限度地使用SSH。2015年,微软宣布将在未来的操作系统中提供原生SSH协议支持[3]。
在设计上,SSH是Telnet和非安全shell的替代品。Telnet和Berkeley rlogin、rsh、rexec等协议采用明文传输,使用不可靠的密码,导致资讯容易遭到监听,也容易通过数据包分析嗅探到[4]。SSH旨在保证非安全网络环境(例如互联网)中资讯加密完整可靠。不过,爱德华·斯诺登泄露的文件也指出,美国国家安全局有时能够把SSH协议传输的资讯解密出来,从而读出SSH会话的传输内容[5]。
2017年7月6日,非营利组织维基解密确认美国中央情报局已经开发出能够在Windows或Linux操作系统中窃取SSH会话的工具。[6]
概述
[编辑]SSH以非对称加密实现身份验证[2]。身份验证有多种途径,例如其中一种方法是使用自动生成的公钥-私钥对来简单地加密网络连接,随后使用密码认证进行登录;另一种方法是人工生成一对公钥和私钥,通过生成的密钥进行认证,这样就可以在不输入密码的情况下登录。任何人都可以自行生成密钥。公钥需要放在待访问的电脑之中,而对应的私钥需要由用户自行保管。认证过程基于生成出来的私钥,但整个认证过程私钥本身中不会传输到网络中。
SSH协议有两个主要版本,分别是SSH-1和SSH-2。无论是哪个版本,核实未知密钥来源都是重要的事情,因为SSH只验证提供用户是否拥有与公钥相匹配的私钥,只要接受公钥而且密钥匹配伺服器就会授予许可。这样的话,一旦接受了恶意攻击者的公钥,那么系统也会把攻击者视为合法用户。
密钥管理
[编辑]在类Unix系统中,已许可登录的公钥通常保存在用户家目录的 ~/.ssh/authorized_keys 文件中[7],该文件只由SSH使用。当远程机器持有公钥,而本地持有对应私钥时,登录过程不再需要手动输入密码。另外为了额外的安全性,私钥本身也能用密码保护。
私钥会保存在固定位置,也可以通过命令行参数指定(例如ssh命令的“-i”选项)。ssh-keygen是生成密钥的工具之一。
SSH也支持基于密码的身份验证,此时密钥是自动生成的。若客户端和服务端从未进行过身份验证,SSH未记录伺服器端所使用的密钥,那么攻击者可以模仿伺服器端请求并获取密码,即中间人攻击。但是密码认证可以禁用,而且SSH客户端在发现新密钥或未知伺服器时会向用户发出警告。
使用
[编辑]SSH的经典用途是登录到远程电脑中执行命令。除此之外,SSH也支持隧道协议、端口映射和X11连接。借助SFTP或SCP协议还可以传输文件[2]。
SSH使用客户端-伺服器模型。伺服器端需要开启SSH守护进程以便接受远端的连接,而用户需要使用SSH客户端与其建立连接。标准端口中的22端口分配给了SSH服务[8]。
大多数现代操作系统(包括macOS、大部分Linux、OpenBSD、FreeBSD、Solaris等系统)都提供了SSH,但Windows系统未自带SSH程序。Windows用户可以使用Cygwin来建立SSH服务。SSH客户端种类很多,包括专有软件、免费软件和开源软件,例如PuTTY和传输文件专用的WinSCP等。
从云计算的角度上讲,SSH能够阻止一些因直接暴露在互联网而产生的安全问题,在解决连接问题上发挥了重要作用。SSH隧道可以在互联网、防火墙和虚拟机之间提供一个安全的通道[9]。
历史
[编辑]1.x版本
[编辑]芬兰赫尔辛基理工大学的塔图·于勒宁发现自己学校存在嗅探密码的网络攻击,便于1995年编写了一套保护资讯传输的程序,并称其为“secure shell”,简称SSH[10],设计目标是取代先前的rlogin、Telnet、FTP[11]和rsh等安全性不足的协议。1995年7月,于勒宁以免费软件的形式将其发布。程序很快流行起来,截至1995年底,SSH的用户数已经达到两万,遍布五十个国家。
1995年12月,于勒宁创立了SSH通信安全公司来继续开发和销售SSH。SSH的早期版本用到了很多自由软件,例如GNU libgmp,但后来由SSH公司发布的版本逐渐变成了专有软件。
截至2000年,已经有两百万用户使用SSH。[12]
OpenSSH和OSSH
[编辑]1999年,开发者们希望使用自由版本的SSH,于是重新使用较旧的1.2.12版本,这也是最后一个采用开放原始码许可的版本。随后瑞典程序员Björn Grönvall基于这个版本开发了OSSH。不久之后,OpenBSD的开发者又在Grönvall版本的基础上进行了大量修改,形成了OpenSSH,并于OpenBSD 2.6一起发行。从该版本开始,OpenSSH又逐渐移植到了其他操作系统上面。[13]
截至2005年,OpenSSH是唯一一种最流行的SSH实现,而且成为了大量操作系统的默认组件,而OSSH已经过时[14]。OpenSSH仍在维护,而且已经支持SSH-2协议。从7.6版开始,OpenSSH不再支持SSH-1协议。
2.x版本
[编辑]2006年,SSH-2协议成为了新的标准。与SSH-1相比,SSH-2进行了一系列功能改进并增强了安全性,例如基于迪菲-赫尔曼密钥交换的加密和基于消息认证码的完整性检查。SSH-2还支持通过单个SSH连接任意数量的shell会话。SSH-2协议与SSH-1不兼容,由于更加流行,一些实现(例如lsh和Dropbear)只支持SSH-2协议。
1.99版
[编辑]RFC 4253规定支持2.0及以前版本SSH的SSH伺服器应将其原始版本标为“1.99”[15]。“1.99”并不是实际的软件版本号,而是为了表示向下兼容。
应用
[编辑]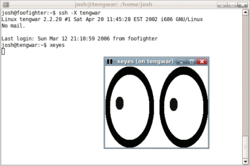

SSH可以用在很多平台上面,例如大多数类Unix系统(如Linux、Solaris、包括macOS在内的BSD等)和Windows系统。SSH能够完成很多任务,例如:
- 远程登录并在远程系统上执行命令;
- 文件传输;
- 与rsync配合,安全地备份、复制文件或制作镜像;
- 建立隧道协议,实现端口映射;
- 实现VPN;
- 将远程系统上的X映射到本机;
- 通过SSH建立的加密SOCKS代理浏览网站;
- 自动化监视与管理远程伺服器;
- 在支持SSH的行动电话或嵌入式装置上进行软件开发。
上述各功能中,有些需要特定的SSH的伺服器或客户端,例如VPN只能通过OpenSSH来实现。
文件传输协议
[编辑]以下几种文件传输方式采用了SSH协议:
Architecture
[编辑]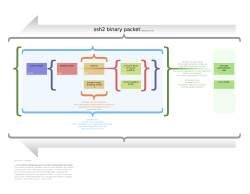
The SSH-2 protocol has an internal architecture (defined in RFC 4251) with well-separated layers, namely:
- The transport layer (RFC 4253). This layer handles initial key exchange as well as server authentication, and sets up encryption, compression and integrity verification. It exposes to the upper layer an interface for sending and receiving plaintext packets with sizes of up to 32,768 bytes each (more can be allowed by the implementation). The transport layer also arranges for key re-exchange, usually after 1 GB of data has been transferred or after 1 hour has passed, whichever occurs first.
- The user authentication layer (RFC 4252). This layer handles client authentication and provides a number of authentication methods. Authentication is client-driven: when one is prompted for a password, it may be the SSH client prompting, not the server. The server merely responds to the client's authentication requests. Widely used user-authentication methods include the following:
- password: a method for straightforward password authentication, including a facility allowing a password to be changed. Not all programs implement this method.
- publickey: a method for public key-based authentication, usually supporting at least DSA or RSA keypairs, with other implementations also supporting X.509 certificates.
- keyboard-interactive (RFC 4256): a versatile method where the server sends one or more prompts to enter information and the client displays them and sends back responses keyed-in by the user. Used to provide one-time password authentication such as S/Key or SecurID. Used by some OpenSSH configurations when PAM is the underlying host-authentication provider to effectively provide password authentication, sometimes leading to inability to log in with a client that supports just the plain password authentication method.
- GSSAPI authentication methods which provide an extensible scheme to perform SSH authentication using external mechanisms such as Kerberos 5 or NTLM, providing single sign-on capability to SSH sessions. These methods are usually implemented by commercial SSH implementations for use in organizations, though OpenSSH does have a working GSSAPI implementation.
- The connection layer (RFC 4254). This layer defines the concept of channels, channel requests and global requests using which SSH services are provided. A single SSH connection can host multiple channels simultaneously, each transferring data in both directions. Channel requests are used to relay out-of-band channel-specific data, such as the changed size of a terminal window or the exit code of a server-side process. The SSH client requests a server-side port to be forwarded using a global request. Standard channel types include:
- shell for terminal shells, SFTP and exec requests (including SCP transfers)
- direct-tcpip for client-to-server forwarded connections
- forwarded-tcpip for server-to-client forwarded connections
- The SSHFP DNS record (RFC 4255) provides the public host key fingerprints in order to aid in verifying the authenticity of the host.
This open architecture provides considerable flexibility, allowing the use of SSH for a variety of purposes beyond a secure shell. The functionality of the transport layer alone is comparable to Transport Layer Security (TLS); the user-authentication layer is highly extensible with custom authentication methods; and the connection layer provides the ability to multiplex many secondary sessions into a single SSH connection, a feature comparable to BEEP and not available in TLS.
改进
[编辑]These are intended for performance enhancements of SSH products:
- SSH-over-SCTP: support for SCTP rather than TCP as the connection oriented transport layer protocol.[16]
- ECDSA: support for elliptic curve DSA rather than DSA or RSA for signing.[17]
- ECDH: support for elliptic curve Diffie–Hellman rather than plain Diffie–Hellman for encryption key exchange.[17]
- UMAC: support for UMAC rather than HMAC for MAC/integrity.[18]
弱点
[编辑]SSH-1
[编辑]In 1998 a vulnerability was described in SSH 1.5 which allowed the unauthorized insertion of content into an encrypted SSH stream due to insufficient data integrity protection from CRC-32 used in this version of the protocol.[19][20] A fix known as SSH Compensation Attack Detector[21] was introduced into most implementations. Many of these updated implementations contained a new integer overflow vulnerability[22] that allowed attackers to execute arbitrary code with the privileges of the SSH daemon, typically root.
In January 2001 a vulnerability was discovered that allows attackers to modify the last block of an IDEA-encrypted session.[23] The same month, another vulnerability was discovered that allowed a malicious server to forward a client authentication to another server.[24]
Since SSH-1 has inherent design flaws which make it vulnerable, it is now generally considered obsolete and should be avoided by explicitly disabling fallback to SSH-1.[来源请求] Most modern servers and clients support SSH-2.[来源请求]
CBC plaintext recovery
[编辑]In November 2008, a theoretical vulnerability was discovered for all versions of SSH which allowed recovery of up to 32 bits of plaintext from a block of ciphertext that was encrypted using what was then the standard default encryption mode, CBC.[25] The most straightforward solution is to use CTR, counter mode, instead of CBC mode, since this renders SSH resistant to the attack.[25]
Undisclosed vulnerabilities
[编辑]On December 28, 2014 Der Spiegel published classified information[5] leaked by whistleblower Edward Snowden which suggests that the National Security Agency may be able to decrypt some SSH traffic. The technical details associated with such a process were not disclosed.
US Government Hack of SSH Protocols Confirmed
[编辑]On 6 July, 2017, the government transparency activist organization WikiLeaks released US Central Intelligence Agency documents that revealed how the CIA's Information Operations Center hacks into "secure" communications that utilize the SSH protocol on both Windows and Linux operating systems. The release included official user guides for the CIA's BothanSpy and Gyrfalcon programmes which "are designed to intercept and exfiltrate SSH credentials but work on different operating systems with different attack vectors" WikiLeaks reported.
"BothanSpy is an implant that targets the SSH client program Xshell on the Microsoft Windows platform and steals user credentials for all active SSH sessions. These credentials are either username and password in case of password-authenticated SSH sessions or username, filename of private SSH key and key password if public key authentication is used. BothanSpy can exfiltrate the stolen credentials to a CIA-controlled server (so the implant never touches the disk on the target system) or save it in an enrypted file for later exfiltration by other means. BothanSpy is installed as a Shellterm 3.x extension on the target machine.
"Gyrfalcon is an implant that targets the OpenSSH client on Linux platforms (centos,debian,rhel,suse,ubuntu). The implant can not only steal user credentials of active SSH sessions, but is also capable of collecting full or partial OpenSSH session traffic. All collected information is stored in an encrypted file for later exfiltration. It is installed and configured by using a CIA-developed root kit (JQC/KitV) on the target machine."[26]
标准文档
[编辑]The following RFC publications by the IETF "secsh" working group document SSH-2 as a proposed Internet standard.
- RFC 4250, The Secure Shell (SSH) Protocol Assigned Numbers
- RFC 4251, The Secure Shell (SSH) Protocol Architecture
- RFC 4252, The Secure Shell (SSH) Authentication Protocol
- RFC 4253, The Secure Shell (SSH) Transport Layer Protocol
- RFC 4254, The Secure Shell (SSH) Connection Protocol
- RFC 4255, Using DNS to Securely Publish Secure Shell (SSH) Key Fingerprints
- RFC 4256, Generic Message Exchange Authentication for the Secure Shell Protocol (SSH)
- RFC 4335, The Secure Shell (SSH) Session Channel Break Extension
- RFC 4344, The Secure Shell (SSH) Transport Layer Encryption Modes
- RFC 4345, Improved Arcfour Modes for the Secure Shell (SSH) Transport Layer Protocol
It was later modified and expanded by the following publications.
- RFC 4419, Diffie-Hellman Group Exchange for the Secure Shell (SSH) Transport Layer Protocol (March 2006)
- RFC 4432, RSA Key Exchange for the Secure Shell (SSH) Transport Layer Protocol (March 2006)
- RFC 4462, Generic Security Service Application Program Interface (GSS-API) Authentication and Key Exchange for the Secure Shell (SSH) Protocol (May 2006)
- RFC 4716, The Secure Shell (SSH) Public Key File Format (November 2006)
- RFC 4819: Secure Shell Public Key Subsystem (March 2007)
- RFC 5647: AES Galois Counter Mode for the Secure Shell Transport Layer Protocol (August 2009)
- RFC 5656, Elliptic Curve Algorithm Integration in the Secure Shell Transport Layer (December 2009)
- RFC 6187: X.509v3 Certificates for Secure Shell Authentication (March 2011)
- RFC 6239: Suite B Cryptographic Suites for Secure Shell (SSH) (May 2011)
- RFC 6594: Use of the SHA-256 Algorithm with RSA, Digital Signature Algorithm (DSA), and Elliptic Curve DSA (ECDSA) in SSHFP Resource Records
- RFC 6668, SHA-2 Data Integrity Verification for the Secure Shell (SSH) Transport Layer Protocol (July 2012)
- RFC 7479: Ed25519 SSHFP Resource Records
In addition, the OpenSSH project includes several vendor protocol specifications/extensions:
参见
[编辑]参考文献
[编辑]- ^ The Secure Shell (SSH) Protocol Architecture. RFC 4251. IETF Network Working Group. 2006-01.
- ^ 2.0 2.1 2.2 The Secure Shell (SSH) Authentication Protocol. RFC 4252. IETF Network Working Group. 2006-01.
- ^ Peter Bright. Microsoft bringing SSH to Windows and PowerShell. Ars Technica. 2015-06-02.
- ^ SSH Hardens the Secure Shell, Serverwatch.com
- ^ 5.0 5.1 Prying Eyes: Inside the NSA's War on Internet Security. Spiegel Online. 2014-12-28.
- ^ BothanSpy. wikileaks.org. 2017-07-06 [2017-09-25].
- ^ SSH setup manual
- ^ Service Name and Transport Protocol Port Number Registry. iana.org.
- ^ Amies, A; Wu, C F; Wang, G C; Criveti, M. Networking on the cloud. IBM developerWorks. 2012.
- ^ Tatu Ylönen. The new skeleton key: changing the locks in your network environment. 2013-04-02.
- ^ Tatu Ylönen. SSH Port.
- ^ Nicholas Rosasco and David Larochelle. How and Why More Secure Technologies Succeed in Legacy Markets: Lessons from the Success of SSH (PDF). Quoting Barrett and Silverman, SSH, the Secure Shell: The Definitive Guide, O'Reilly & Associates (2001). Dept. of Computer Science, Univ. of Virginia. [2006-05-19].
- ^ OpenSSH: Project History and Credits. openssh.com. 2004-12-22 [2014-04-27].
- ^ OSSH Information for VU#419241
- ^ RFC 4253, section 5. Compatibility With Old SSH Versions. RFC 4253. IETF Network Working Group. 2006-01.
- ^ Seggelmann, R.; Tuxen, M.; Rathgeb, E.P. SSH over SCTP — Optimizing a multi-channel protocol by adapting it to SCTP. Communication Systems, Networks & Digital Signal Processing (CSNDSP), 2012 8th International Symposium on. 18–20 July 2012: 1–6. ISBN 978-1-4577-1473-3. doi:10.1109/CSNDSP.2012.6292659.
- ^ 17.0 17.1 Stebila, D.; Green J. RFC5656 - Elliptic Curve Algorithm Integration in the Secure Shell Transport Layer. December 2009 [2012-11-12].
- ^ Miller, D.; Valchev, P. The use of UMAC in the SSH Transport Layer Protocol / draft-miller-secsh-umac-00.txt. 2007-09-03 [2012-11-12].
- ^ SSH Insertion Attack
- ^ Weak CRC allows packet injection into SSH sessions encrypted with block ciphers, US-CERT
- ^ SSH CRC-32 Compensation Attack Detector Vulnerability, SecurityFocus
- ^ SSH CRC32 attack detection code contains remote integer overflow, US-CERT
- ^ Weak CRC allows last block of IDEA-encrypted SSH packet to be changed without notice, US-CERT
- ^ SSH-1 allows client authentication to be forwarded by a malicious server to another server, US-CERT
- ^ 25.0 25.1 SSH CBC vulnerability, US-CERT
- ^ BothanSpy. www.wikileaks.org. 2017-07-06 [2017-07-09].
扩展阅读
[编辑]- Daniel J. Barrett, Richard E. Silverman, and Robert G. Byrnes, SSH: The Secure Shell (The Definitive Guide), O'Reilly 2005 (2nd edition). ISBN 0-596-00895-3
- Michael Stahnke, Pro OpenSSH, Apress 2005 ISBN 1-59059-476-2
- Tatu Ylönen. Announcement: Ssh (Secure Shell) Remote Login Program. comp.security.unix. 1995-07-12. Original announcement of Ssh
- Himanshu Dwivedi; Implementing SSH, Wiley 2003. ISBN 978-0-471-45880-7
- 本条目部分或全部内容出自以GFDL授权发布的《自由在线电脑词典》(FOLDOC)。
